You’re not selling antivirus software or firewalls – you’re selling confidence, protection, and control in a digital world. Your potential clients are CISOs and IT Directors. They don’t find solutions through ads. They research technologies and compare vendors for specific, critical tasks: securing cloud infrastructure and data, monitoring and preventing data leaks, managing incidents, responding to attacks, and ensuring GDPR compliance. If your website doesn’t appear when they search for answers to these problems, you’ve lost their attention before the conversation even starts.
Specialized SEO transforms your website into a tool for building trust. It allows you to demonstrate deep expertise precisely when a prospective client is searching for a concrete solution. It addresses their doubts and positions you where real, high-value purchasing decisions are made.
This article is your practical, step-by-step playbook. We’ll break down exactly how cybersecurity SEO works, why generic approaches fall flat, and how to build a system that consistently generates qualified leads. You’ll get actionable steps, not vague theory.
SEO for Cybersecurity Companies: What It Is, Why You Need It, and How It Works
SEO for cybersecurity companies is a system designed to make your specialized expertise visible to the people who need it, at the moment they need it. It turns your website into a round-the-clock expert and lead generator. Let’s dive into how this works in the real world.
What is Cybersecurity SEO and Its Role in Attracting B2B Clients
Cybersecurity SEO is the process of optimizing your company’s website to attract highly targeted traffic, not just general visitors. Your target audience is technical specialists, security leaders, and decision-makers within other businesses.
The core purpose of this SEO is lead generation for cybersecurity SEO. When your site ranks for complex, niche technical queries, you attract visitors who are already deeply informed. They know their specific problem and are actively evaluating solutions. Your job is to be the definitive answer. A well-executed strategy turns your site into a sales asset that works continuously, effectively supplementing or even replacing outbound efforts.
How SEO for IT Security Differs from Standard SEO
Standard SEO often chases volume: more traffic is assumed to be better. In the B2B cybersecurity space, that’s a flawed metric. Thousands of visitors looking for “free antivirus download” will never convert into enterprise sales.
SEO for IT security companies operates on a different set of rules and comes with unique challenges.
| The Challenge | What It Means | The Practical Impact |
|---|---|---|
| Fierce Competition | The top results are often dominated by sites with massive budgets, major media outlets, and analyst firms. | Ranking for broad terms like “cybersecurity” is incredibly difficult. Success requires a focused, strategic approach. |
| Long & Complex Sales Cycles | Purchasing decisions can take anywhere from 3 to 12 months, involving multiple stakeholders. | You almost never see a query like “buy enterprise firewall.” You must engage with informational queries (“how to secure a hybrid cloud,” “ransomware recovery steps”) to guide buyers over a long period. |
| Content Must Be Flawlessly Expert | Any error in terminology or reliance on outdated information instantly destroys credibility with a technical audience. | Writers must either have deep subject-matter expertise or work in lockstep with your technical team. Rigorous fact-checking is non-negotiable. |
| Technical Hurdles | Security company websites often have complex architectures, client portals, and password-protected areas. | The technical side of cybersecurity website optimization is paramount. A single indexing error can block your entire SEO effort. |
The data underscores this need: according to BusinessDasher, 90% of B2B buyers search online for suppliers, and 71% start their process with a generic Google search. Being found in these searches isn’t optional; it’s essential.
How Your Ideal Client Actually Searches: From Problem to Purchase
The journey to buying a complex B2B security solution isn’t a straight line. A CISO doesn’t wake up thinking, “I need to purchase a SIEM today.” First, they recognize a threat or a gap. Then they explore ways to address it, compare specific solutions, and finally evaluate potential partners.
Your cybersecurity SEO strategies must cover every leg of this journey. If you only try to catch buyers at the final “purchase” stage, you’re missing the vast majority of opportunities. Let’s walk through this process from the client’s point of view.
Who is Searching for Security Services and How Decisions Are Made
Typically, two key roles drive the search. First, the technical evaluators (Security Engineers, DevOps). They hunt for specific technologies, integration details, and technical documentation. Their goal is to find the most effective technical solution. Second, the executive decision-makers (CISO, IT Director). They’re focused on business alignment, ROI, risk mitigation, and reporting. They need to justify the investment.

The decision is never rushed. It involves awareness, market research, vendor shortlisting, RFPs, and often pilot projects. At every single step, the client is online, searching for information. Your SEO must be there to answer their evolving questions, build credibility, and gently steer them toward a conversation with your sales team.
Guiding Clients Through the B2B Funnel
Choosing a cybersecurity partner is a multi-stage process. Your role is to be a helpful guide at each step, providing the right information at exactly the right time. (We’ll cover specific content formats later – here, we focus on the stages).
- Top of the Funnel (Awareness & Consideration). The client recognizes a problem and is exploring what’s possible. Here, your best tool is genuinely helpful, expert content that educates without a hard sell. The goal is to attract visitors and establish your brand as a knowledgeable authority. Think blog articles, threat analyses, and podcasts. The call-to-action should be soft: “Subscribe for updates,” “Download our threat landscape report.”
- Middle of the Funnel (Evaluation & Decision). The client has defined their need and is now comparing specific solutions and vendors. Your content should help them make an informed choice while showcasing your strengths. This is where detailed case studies, comparison guides, and expert webinars shine. The goal is to prove your competence, and the CTA moves toward deeper engagement: “Request a custom case study review,” “Schedule a technical deep-dive.”
- Bottom of the Funnel (Action). The client is ready to move forward. Your task is to make the next step effortless and eliminate final objections. Content here is openly commercial but still valuable. This includes detailed service pages, product demo videos, and formal proposal pages. The CTA is direct: “Request a Live Demo,” “Contact Sales for a Quote,” “Start Your Free Trial.”
By mapping your content to this journey, you systematically nurture a visitor from a state of curiosity to becoming a sales-ready lead. This is the essence of driving organic growth in cybersecurity.
Keywords and Strategies to Grow Your Cybersecurity Traffic
Basic SEO tactics might bring visitors, but in B2B security, they rarely bring results. To truly increase traffic to your cybersecurity site, you need to understand how CISOs and engineers phrase their problems.
Let’s get practical. We’ll examine the types of queries that matter, the tools for finding them, and how to analyze your competitors to find a path to the top of the search results.
Understanding Search Intent: Informational, Commercial, Transactional
Every search query reveals the user’s underlying goal, or search intent. For your SEO and content, keywords are signals about what the searcher wants. Recognizing intent is crucial for cybersecurity SEO.
The three primary types:
- Informational. The user is learning about a problem. Queries: “what is endpoint detection and response,” “SOAR vs. SIEM differences,” “GDPR compliance checklist for SaaS.” Your content’s goal here is to attract and educate.
- Commercial. The user knows what they need and is comparing options. Queries: “best cloud security posture management tools 2026,” “compare managed detection and response providers,” “top cybersecurity vendors for financial services.” Here, you need in-depth comparisons, analyst reports, and vendor selection guides.
- Transactional. The user is ready to take a specific action. Queries: “hire a penetration testing firm,” “request a quote for security awareness training,” “schedule a vulnerability assessment.” Content here must facilitate the action, with clear CTAs for demos, consultations, or quotes.
Effective cybersecurity website optimization requires a mix of all three. Focusing only on one creates an imbalance: lots of traffic but no leads, or vice versa.
Search volume also plays a role. High-volume, broad terms (“cybersecurity”) are ultra-competitive and attract diverse audiences. Long-tail, specific queries (“SOC 2 Type II compliance for healthcare startup”) bring less traffic, but the visitors are far more targeted and often further down the buying path.
A smart strategy balances both: broad terms for brand visibility, and specific long-tail queries for lead generation.
Keyword Research for Cybersecurity Firms
Start with a brain dump. List every core term related to your services: “audit,” “compliance,” “incident response,” “threat intelligence.” Then, leverage professional tools.
For global markets, platforms like Ahrefs, Semrush, and Moz are industry standards. They show search volume, competition, related terms, and trends. Free tools like Google Keyword Planner (good for direction, less for precise volume) and Ubersuggest can provide a starting point.
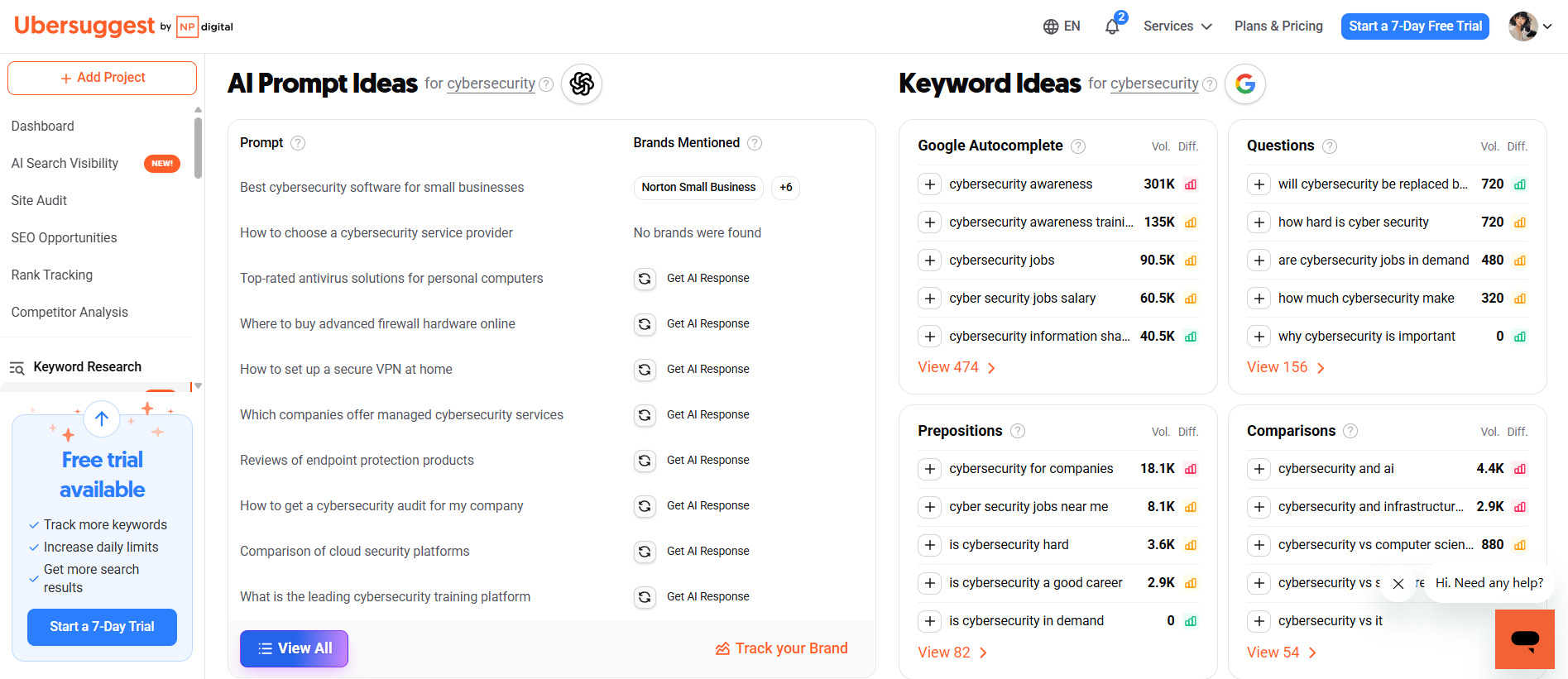
The workflow:
- Gather. Use tools and spy on competitors to build a massive initial list of potential keywords.
- Clean. Ruthlessly remove anything irrelevant (e.g., consumer-grade terms if you sell to enterprises).
- Cluster. Group keywords by common theme and funnel stage. One cluster might be “cloud security audit,” another “API security testing.”
- Map. Assign each keyword cluster to a specific page on your site. This creates a logical site architecture and forms the basis of your cybersecurity website optimization.
This organized collection is your semantic core – the blueprint for all your SEO efforts.
Competitor Analysis: Learning from Their Success and Finding Gaps
A cybersecurity website SEO audit starts by looking at who’s already winning. Your goal is to decode their success and identify weaknesses or opportunities they’ve missed.
First, define your competitors. They’re not just other security vendors. They can include major tech companies with security divisions, IT consultancies, and industry publications.
Let’s use Palo Alto Networks, a clear market leader, as an example.
What to analyze:
- Their Keywords and Content. What terms are they ranking for? Which articles, guides, or resources drive the most organic traffic? Study their page titles (H1), meta descriptions, and subheadings. This reveals gaps in your own content plan.
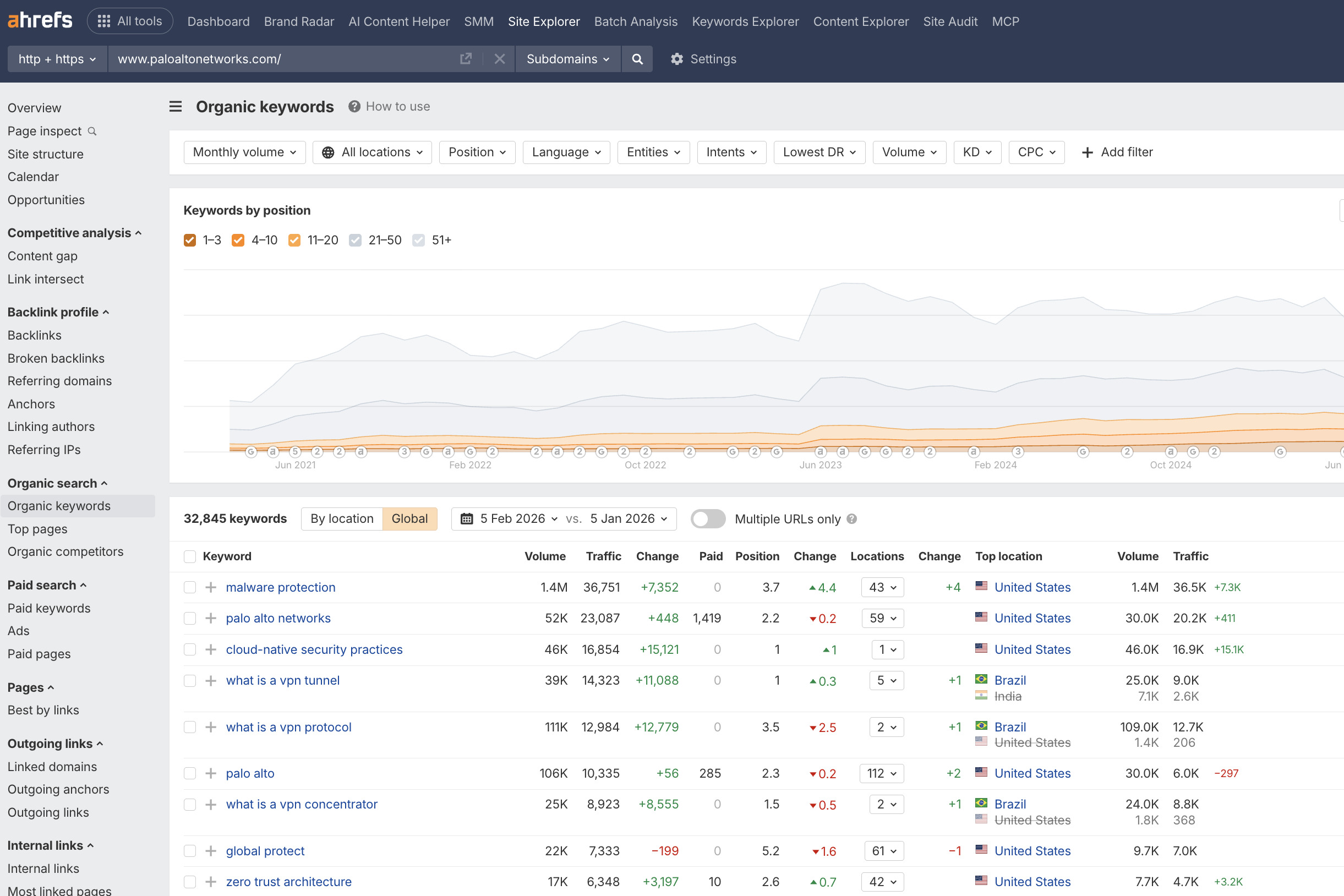
- Technical Performance. How fast does their site load, especially on mobile? Is it technically sound? Use tools like PageSpeed Insights and Screaming Frog. A slow, buggy site is a vulnerability you can exploit.
- Link Profile (Backlinks). Which high-authority sites (like Gartner, DarkReading, or universities) link to them? The quality and relevance of these links are a huge ranking factor. This shows you where to focus your own link-building efforts.
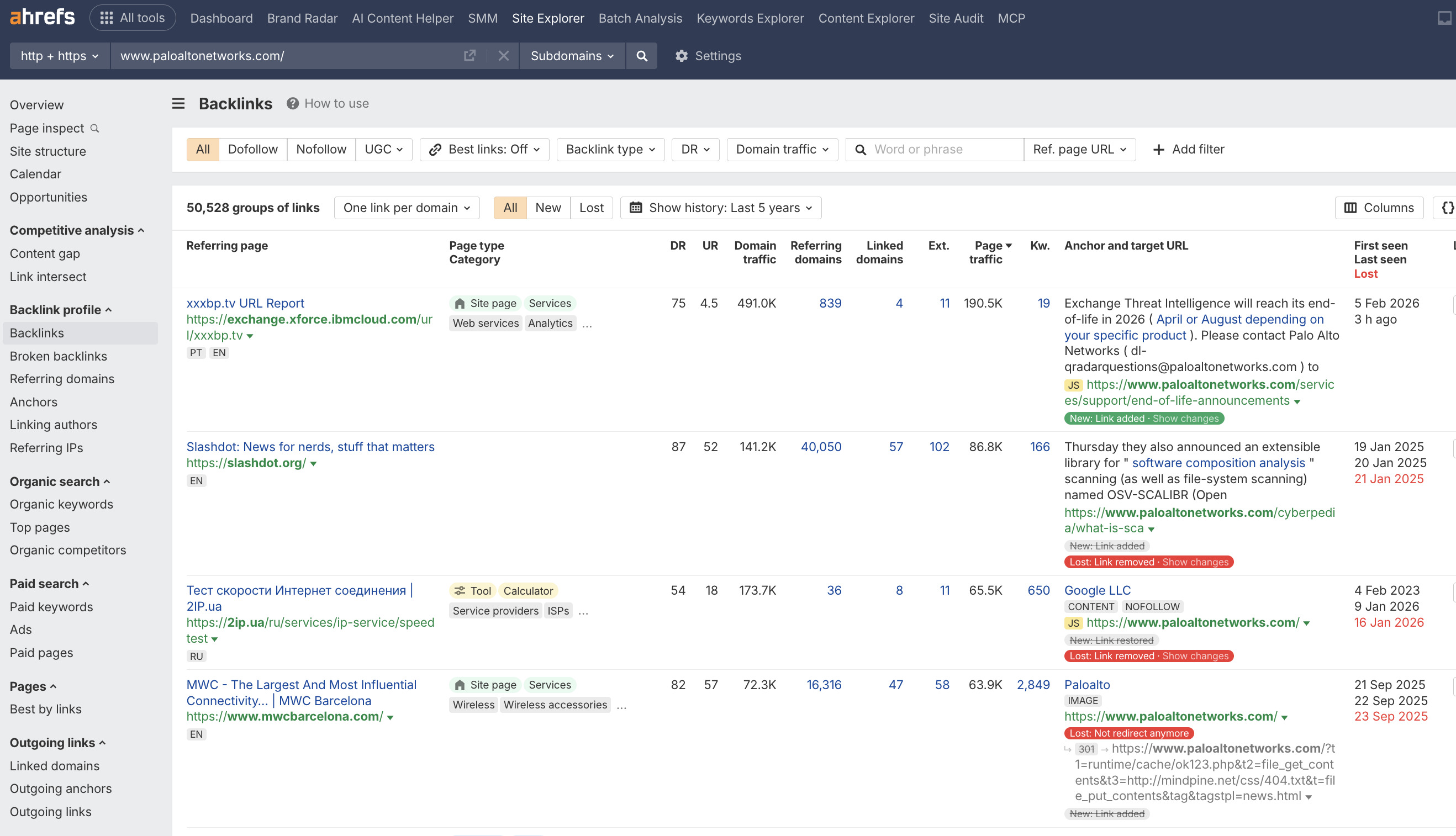
- User Experience (UX). Is their site easy to navigate? Are service pages clear? Do they showcase testimonials and case studies effectively? Is the path to contact obvious? B2B SEO cybersecurity fails if the site experience doesn’t guide users toward conversion.
Use the same SEO platforms (Ahrefs, Semrush) for this analysis. Also, check your own Google Search Console to see what queries are already sending you traffic – it’s a goldmine of intent data.
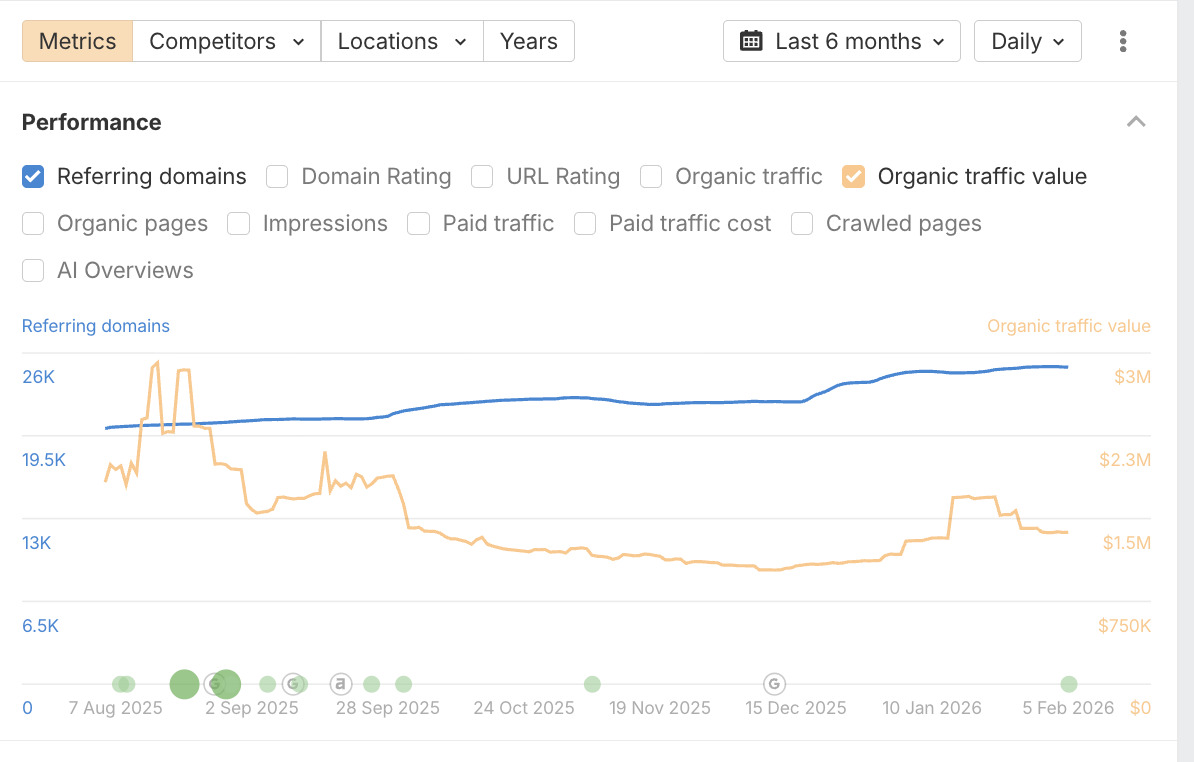
Next, we’ll look at how to build and optimize your website’s technical foundation to support this strategy.
Technical and On-Page SEO for Your Cybersecurity Website
Technical and on-page SEO is the detailed, unglamorous work that makes everything else possible. Without it, even brilliant content can be hidden by slow speeds, poor structure, or technical errors.
Technical SEO Foundations for IT Companies
Technical SEO is about making your website easily readable and indexable by search engines. For a B2B tech company, it’s also a signal of professionalism.
Key areas to optimize:
- Speed & Performance. Page load time is a direct Google ranking factor. A slow site drives visitors away and hurts your rankings. Test with PageSpeed Insights or GTmetrix. Optimize images, leverage browser caching, minify code, and invest in quality hosting.
- Mobile-First. Most searches are on mobile. Your site must be fast and flawless on smartphones and tablets. This is non-negotiable.
- Security (HTTPS). For a cybersecurity firm, not having HTTPS is unthinkable. It’s a basic trust signal for users and a ranking factor for Google.
- Clean Indexing. Ensure Google can crawl and index all your important pages. Your robots.txt file should be configured correctly, and critical pages shouldn’t be blocked. An XML sitemap helps search engines discover your content.
- Structured Data (Schema). Adding Schema.org markup helps search engines understand your content better. For security services, use schemas like
Service,Organization, orFAQPage. This can unlock rich snippets in search results, making your listing more prominent.
Local SEO: Google Business Profile for Offices
If you serve local markets or have physical offices, your Google Business Profile (GBP) is a must-have. It powers your presence in Google Search and Maps for local queries.
How to optimize your GBP:
- Complete Every Field. Use your exact business name, address, phone, website, hours, and correct category (e.g., “Cybersecurity Service”).
- Craft a Compelling Description. Naturally include your key services and location focus (e.g., “Managed security services for businesses in Chicago and the Midwest”).
- Add Photos & Updates. Regularly post photos of your team, office, and events. Share updates about new services or content.
- Manage Reviews. Proactively ask happy clients for reviews. Respond professionally to every review, good or bad. It shows you’re engaged.
- Use the “Posts” Feature. Share links to new blog posts, announce webinars, or promote offers to keep your profile active.
A well-optimized GBP captures leads searching for “cybersecurity company near me” or “IT security services [City Name].”
On-Page Optimization: Structure, Content, and Metadata
On-page optimization is about shaping individual pages to be highly relevant to target queries and persuasive to visitors.
- Clear Site Architecture. Organize your site logically. Common sections: Services, Case Studies, Blog/Resources, About, Contact. Use clear navigation menus and breadcrumb trails.
- Powerful Service Pages. These are your key commercial pages. Each needs a compelling H1, detailed benefit-focused copy (not just features), social proof (case studies, logos, testimonials), and a strong, clear call-to-action.
- Optimize Meta Tags. The page title (title tag) and meta description are your ad in the search results. The title should include the primary keyword and be click-worthy. The description should be a persuasive snippet that encourages clicks.
- Optimize for Evolving Search. With the rise of AI-powered search and Generative Engine Optimization, providing direct, structured answers is key. Use clear introductions, bulleted lists, and FAQ sections marked up with Schema.
- Optimize Visuals. Image optimization matters. Use descriptive file names (e.g.,
zero-trust-network-access-diagram.png) and fill in alt text that describes the image. Great infographics can earn valuable backlinks.
The Cybersecurity Website Audit: Finding Your Growth Levers

Conducting a regular cybersecurity website SEO audit is how you stay on track. It helps you fix issues and uncover new opportunities. Aim to do this quarterly.
Focus on these areas:
- Technical Errors: Find and fix broken links, duplicate content, crawl errors, and JavaScript issues.
- User Behavior: Analyze pages with high bounce rates or low time-on-page. This often points to content that doesn’t match search intent or a poor user experience.
- Content Freshness: Update old guides, reference new regulations (like NIST 2.0), and ensure all information is current. Stale content loses authority.
- Ranking Changes: Identify which keywords you’ve lost ground on and find new, relevant queries to target.
- Competitive Moves: Keep an eye on new competitors in the rankings and any shifts in their strategy.
A technically sound, well-optimized website is the reliable platform that supports all your other marketing efforts.
Content That Actually Ranks and Converts in Cybersecurity
You can have the most perfectly optimized site, but without high-quality content, it’s an empty storefront. In B2B security, clients aren’t just browsing – they’re looking for proof you can solve their complex, high-stakes problems.
Digital marketing and SEO for cybersecurity demand content that aligns perfectly with what the user is looking for at each stage of their journey. You can’t offer a price quote to someone just learning about a threat, and you can’t win a deal with a superficial blog post. Your content must answer the immediate question, provide genuine value, and guide the user to the logical next step.
The Synergy of Content Marketing and SEO

Content marketing and SEO are inseparable partners. SEO ensures you can be found. Content marketing gives people a reason to choose you once they arrive. It builds the trust that turns a visitor into a lead.
Central to this is Google’s E-E-A-T framework (Experience, Expertise, Authoritativeness, Trustworthiness). For a security firm, your content is the primary evidence for these criteria. You prove them not by claiming to be experts, but by demonstrating it through:
- Experience: Sharing real-world insights from your work.
- Expertise: Displaying deep, accurate technical knowledge.
- Authoritativeness: Being cited and referenced by other industry authorities.
- Trustworthiness: Maintaining transparency, security, and honesty.
Creating content that achieves this requires skilled, knowledgeable writers who understand the nuance of the field.
Expert Content Formats That Generate Leads
Different content types serve different purposes in the buyer’s journey. A mix is essential.
- Expert Articles & Research (Top of Funnel). Goal: Attract those discovering a problem. This content answers broad, informational questions. Examples: “What is a Software Supply Chain Attack?”, “2026 Outlook: AI-Powered Security Threats.” This builds initial brand authority and attracts traffic.
Example: Zscaler’s article “What Is a Supply Chain Attack?”
- Deep-Dive Guides, White Papers, Webinars (Middle of Funnel). Goal: Nurture prospects who are evaluating solutions. This content helps them compare and make informed decisions. Examples: “The Ultimate Guide to Implementing a Zero Trust Model,” “Webinar: Benchmarking Your SOC’s Performance.” This is often gated content (exchanged for contact info), making it a powerful lead magnet.
Example: Absolute Software’s webinar on Zero Trust Architecture.
- Case Studies, Demos, & Product Pages (Bottom of Funnel). Goal: Convince and convert the ready-to-buy prospect. This content provides the final proof and facilitates action. Examples: “Case Study: How We Helped a FinTech Achieve SOC 2 in 90 Days,” dedicated “Request a Demo” page. This content removes final barriers to sale.
Example: Wizard Cyber’s case study for a consumer goods client.
To amplify this content, strategic outreach is key. This means proactively getting your research in front of journalists, pitching your experts for quotes, or contributing guest posts to authoritative industry sites. Effective outreach builds links, brand awareness, and drives direct referral traffic.
Building Authority with Content Clusters and Internal Linking
To organize this content for maximum SEO impact, use the thematic cluster model.
- Choose a core, “pillar” topic (e.g., “Ransomware Protection”).
- Create multiple in-depth pieces (“cluster content”) that explore subtopics (e.g., “How Ransomware Spreads,” “Ransomware Recovery Checklist,” “Case Study: Ransomware Attack on a Manufacturer”).
- Link all cluster pages thoroughly to the pillar page and to each other with internal links.
This model delivers a triple win for SEO for IT security companies:
- For Users: They get a comprehensive resource hub, encouraging deeper exploration and longer site visits.
- For SEO: Search engines clearly see the depth of your coverage on a topic, significantly boosting the authority of your pillar page for competitive terms.
- For Business: You create a natural pathway that guides users from problem awareness to your specific solution, systematically fueling lead generation for cybersecurity SEO.
This approach turns your blog from a collection of posts into a structured, interlinked knowledge base that search engines – and clients – love.
Link-Building, Trust, and Authority in Cybersecurity
In cybersecurity, trust is your most valuable currency. Clients must trust you with their crown jewels. Search engines use a similar logic: to decide if your site deserves a top spot, they look for external votes of confidence.
The most powerful vote is a link from a respected, relevant website. Link-building is the systematic process of earning these links, and in security, it’s not optional – it’s essential.
Why Links Are Non-Negotiable for Cybersecurity SEO
To Google, a quality backlink is a recommendation. If an industry publication like DarkReading, a research firm like Gartner, or a renowned expert links to your site, it’s a strong signal that your content is authoritative and trustworthy.
This is especially critical in security for three reasons:
- The Competition is Elite. The top spots are held by established players with massive resources and existing authority. Good content alone often isn’t enough to displace them without a strong link profile.
- Proof of Real-World Expertise. A link from another recognized expert in your field is the ultimate third-party validation of your own expertise.
- Direct, Qualified Traffic. A link from a relevant site isn’t just for SEO “juice” – it sends highly targeted visitors who already trust the source, giving you a warm audience from the start.
A robust link profile is what often separates websites that rank for high-intent, commercial queries that drive real lead generation from those that don’t.
Safe, Effective Link-Building Strategies for B2B Security
In B2B, where reputation is everything, only white-hat, relationship-driven strategies are sustainable. Black-hat tactics risk permanent penalties.
- Create Unmissable “Linkable Assets.” Develop resources so useful that people naturally want to reference them. Think original research reports (“State of Cloud Security 2026”), comprehensive interactive tools (a “Risk Assessment Calculator”), or definitive, visual guides.
Example: A company risk calculator on Cyber.Irish serves as a prime linkable asset.
- Strategic Guest Posting. Write authoritative articles for the publications your audience reads (CSO Online, The Hacker News, Infosecurity Magazine). The goal is to provide genuine value; a relevant, contextual link in your bio is the reward.
Example: A guest post from Palo Alto on CSO Online.
- The “Broken Link Building” Tactic. Find broken links on authoritative industry sites that used to point to content similar to yours. Create a better, updated version on your site and politely inform the site owner, offering your resource as a replacement. It’s a helpful service that often earns a link.
- Niche Edits/Link Insertions. Identify existing, high-performing articles on relevant sites that could be improved by mentioning your unique data, tool, or case study. Propose a small, value-adding edit that includes a link to your resource.
This kind of link-building requires patience and skill, but the resulting profile is durable and constantly compounds, strengthening your ability to increase traffic to your cybersecurity site.
Digital PR for Cybersecurity Authority
Digital PR is the modern approach to earning media coverage and digital mentions. It’s a powerhouse for building the authority needed to rank a cybersecurity website.
How it works in practice:
- Data-Driven Stories & Expert Commentary. Proactively pitch journalists your unique research data or offer your CTO as an expert source for breaking news on a new vulnerability or regulatory change. Become a go-to source for insight.
- Get Featured in Industry Reports & Roundups. Submit your company and products for consideration in “Top 10” lists, analyst reports (like Gartner Cool Vendors), or vendor comparison articles.
- Leverage Partner & Client Ecosystems. Earn natural mentions through joint case studies with clients or technology partnership announcements.
Effective link-building and PR require a blend of SEO knowledge, media savvy, and persistence. If this isn’t your team’s core competency, partnering with experts is a smart investment.
This is where LinkBuilder.com specializes. We provide link-building services tailored for B2B sectors, with deep expertise in cybersecurity.
We take the time to understand your specific audience and target the publications, blogs, and research hubs they truly trust. We have cultivated relationships within this ecosystem.
Our focus is on quality over quantity, securing placements that build genuine, long-term domain authority. This creates the foundation for sustainable traffic and trust.
Ready to make your website an undeniable authority for both search engines and security leaders? Schedule a consultation to build a strategy that delivers measurable business growth.
Measuring What Matters: Analytics for Cybersecurity SEO
Building an SEO strategy is step one. Without tracking performance, you’re flying blind. Proper analytics transforms SEO from a cost center into a managed engine for lead generation and revenue.
Key Metrics for Cybersecurity Companies
Track a balanced dashboard that connects SEO activity to business outcomes.
| What to Measure | Key Performance Indicators (KPIs) | Tools to Use |
|---|---|---|
| Search Visibility | Rankings for target keywords, # of keywords in top 10, organic traffic volume, search impressions. | Google Search Console, Semrush, Ahrefs. |
| Technical Health | Core Web Vitals scores (LCP, FID, CLS), page load speed, crawl errors, broken links. | Google Search Console, PageSpeed Insights, Screaming Frog. |
| Link Profile Strength | Domain Rating (DR) / Domain Authority (DA), quantity & quality of new referring domains, anchor text diversity. | Ahrefs, Semrush, Majestic. |
| Audience Engagement | Pages per session, average session duration, bounce rate (context-dependent). | Google Analytics 4. |
| Conversions & Revenue | Leads from organic search (form fills, demo requests), organic conversion rate, cost per lead (CPL) from SEO, revenue attributed to organic channels. | Google Analytics 4, your CRM (HubSpot, Salesforce), marketing automation platform. |
Connecting SEO to Sales and ROI
For B2B with long cycles, attribution is key.
- Set Up End-to-End Tracking. Use UTM parameters on all internal links and campaigns. In GA4, configure events and conversions for key actions like “Whitepaper Download” or “Contact Form Submit.”
- Use Multi-Touch Attribution. Don’t just credit the “last click.” Analyze assisted conversions to see how top-funnel blog posts contribute to eventual sales that close months later via a direct visit or sales outreach.
- Calculate ROI. The formula is straightforward:
(Revenue from SEO Leads - SEO Investment) / SEO Investment. Compare the lifetime value (LTV) of SEO-sourced customers to other channels. Quality SEO provides compounding returns over time.
Conduct a formal review of these metrics quarterly to refine your strategy.
Your Action Plan: Implementing SEO for IT Security
Effective cybersecurity SEO is a marathon, not a sprint. It’s a long-term commitment to building digital authority. Success hinges on choosing the right path: building deep in-house capability or partnering with specialists.
Core Strategies for Cybersecurity SEO in 2026
Your cybersecurity SEO 2026 strategy should integrate these five pillars:
- E-E-A-T Driven Content Marketing. Google prioritizes Experience, Expertise, Authoritativeness, and Trustworthiness. In security, this is everything. Move beyond generic articles. Produce content that shows lived experience, deep technical understanding, and earns recognition from peers. Avoid AI-generated fluff without heavy expert review.
- Technical Excellence as a Baseline. Your site must be fast, secure (HTTPS), mobile-perfect, and easily crawlable. This is the non-negotiable foundation of cybersecurity website optimization. Schema markup for services and FAQs can give you an edge in search results.
- Optimize for AI and Answer Engines. Search is evolving with AI Overviews and rich snippets. Structure your content to provide direct, concise answers. Use clear headers, bulleted lists, and a strong introductory summary.
- Don’t Neglect Local SEO (If Applicable). If you have offices or serve specific regions, a fully optimized Google Business Profile is a must. It drives visibility for “near me” searches and builds local trust.
- Adopt the Topic Cluster Model. Organize your content into pillars and clusters (e.g., a pillar page on “Data Loss Prevention” supported by clusters on “DLP for email,” “cloud DLP,” “case studies”). This creates a powerful internal linking structure that signals topical authority to Google.
Implementing these SEO tips for cybersecurity firms systematically will transform your website from a digital brochure into your most effective lead generation channel.
How to Choose an SEO Partner for a Cybersecurity Firm

The niche is too complex for generic marketing agencies. You need a partner who speaks the language of both SEO and security.
Evaluate potential partners on these criteria:
- Proven B2B & Cybersecurity Experience. This is the first filter. Ask for specific case studies showing traffic and lead growth for security clients. They should understand your audience’s pain points and search behavior intuitively.
- Holistic, Integrated Methodology. Avoid “link-only” or “content-only” shops. The partner should offer a full-funnel approach: technical audit, keyword strategy, expert content creation, and authoritative link-building.
- Transparency & Realistic Expectations. Be wary of anyone promising #1 rankings in weeks. A credible partner will outline a phased plan (e.g., months 1-3: foundation, months 4-9: growth) and explain why it takes time.
- Team Expertise & Access. Who will do the work? Do they have writers or strategists with a technical background? Will you have direct access to them?
- Business-Outcome Focus. The conversation should be about leads, pipeline influence, and revenue – not just rankings and traffic. Their reporting should connect these dots.
Why LinkBuilder.com is the Right Partner for Cybersecurity SEO
LinkBuilder.com is built for this challenge. We specialize in building authority for complex B2B companies in competitive fields like cybersecurity.
- We Start with Your Audience. We don’t use generic tactics. We analyze what security leaders read, which forums they trust, and what questions they ask. Our outreach targets those exact channels.
- We Build Strategy, Not Just Links. We integrate our link-building into your overall SEO and content strategy, focusing on quality placements that boost your Domain Rating (DR) – a critical metric for outranking entrenched competitors.
- We Integrate our Services into Comprehensive SEO. Our services are a powerful addition to the foundation of technical optimization and expert content. We help accelerate natural recognition of your site by search engines.
- We Focus on Transparency and Long-Term Relationships. We work towards measurable results in visibility growth, traffic, and, consequently, in the number of incoming inquiries from interested clients.
Want to build a website that security decision-makers find, trust, and contact? Book a call to discuss a custom strategy designed for the unique demands of the cybersecurity market.









